vaulient2
New Member
- Mar 12, 2013
- 27
- 3
1st Step:
You will want to purchase a proxy from the DDOS range, these can be found:
These servers are located in the US and are ideal for US based emulation servers.
When buying the DDS protection you will be guided to a popup which would option you to enable SSL and ipv6. They are not important for Habbo Retro, they may however be useful if you are going to run your site through the proxy as well. However these features are beyond the scope of this tutorial.
2nd step:
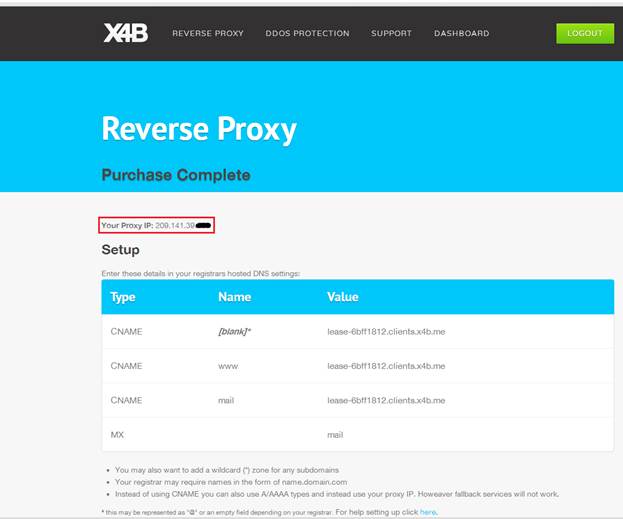
Once you completed the purchase process, you will be brought to the purchase complete page where it will ask you to edit your domain DNS settings. That is not necessary when it comes to a Habbo Retro, as the client does not connect using a domain name. Only people who are also hosting their site on the DDOS protection need to follow these instructions. So I would suggest you to ignore them to begin with.
3rd step:
Navigate to the dashboard, click on the services page in below dashboard in the header. Next to your service IP is an actions drop down. Click on edit in this dropdown.
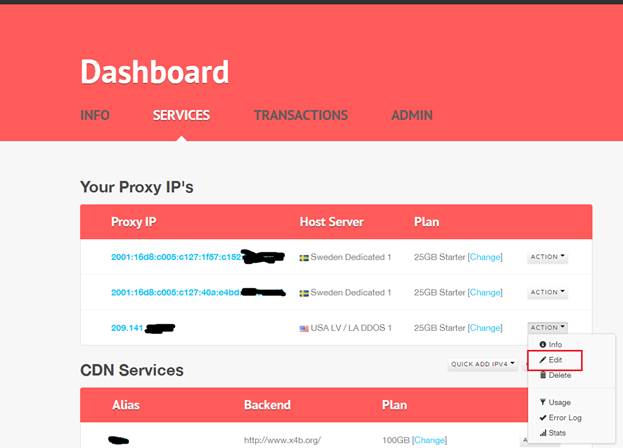
After you have clicked on edit, you should be having a page like this
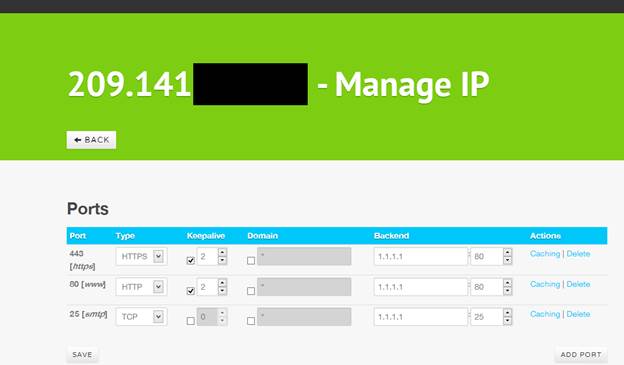
Your service currently contains all the default ports required for a proxying (protecting) a web page and mail service. However it does not have the ports required for a Habbo retro. To add these ports first delete the existing ports, this is optional but recommended since you won’t be using them. Then click the add port button and fill out the following settings.

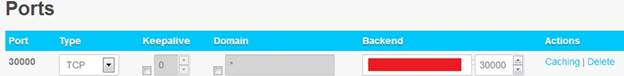
Where 30000 is, is your hotel port. And where “YOUR-IP” is your hotel IP. When done click and and your settings should now look something like below.
4th Step:
Now that you have configured your TCP proxy click on save. Now go back to your CMS and head towards your client.php (for REVCMS) and for UberCMS it should be in class.config.php or ubercms_config.php for UberCMS 2.0.1. Now search for your connection info host.
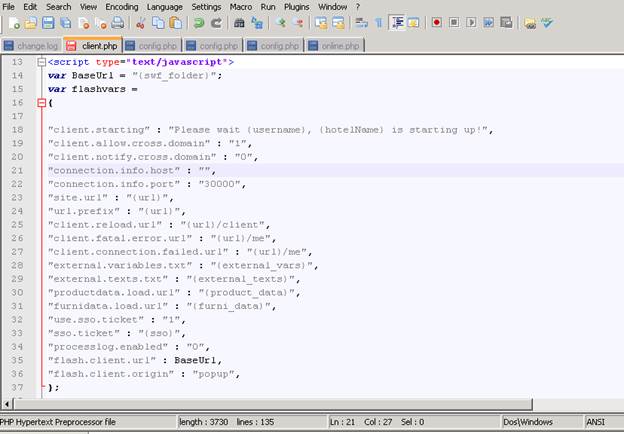
This is my client.php it looks like this (above), it should look similar for others as well.
Put your proxy IP in your connection.info.host and the connection.info.port should be 30000 (or whatever you entered on X4B), in the end it should look something like this:
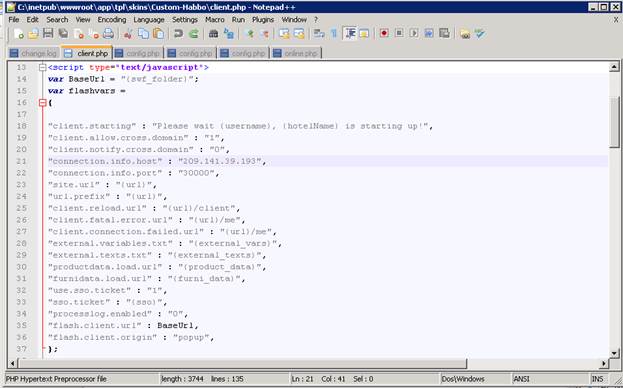
Save your client.php and you are done.
NOTES / DEBUGGING:
You might be wondering what IP should be the server IP in your config, well it should be your VPS IP. With your client IP proxied , nobody can get your real IP so there is no need to worry and what about the emu ? That should be your server IP as well. In your emu config , your game.tcp.port must be must match the port you entered on X4B.
Are you using phoenix emulator? Well there is no need to worry about it at all, since your TCP port has to be 1232 since Aaron forced it to be that way. Just replace all references to port 30000 in this tutorial with 1232.
For more information see:
Conclusion:
Save your client.php and start your emulator , then click on enter client on your hotel and you should be logged on like me:
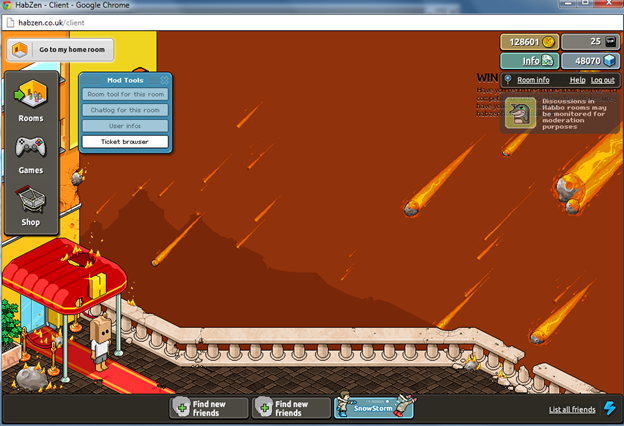
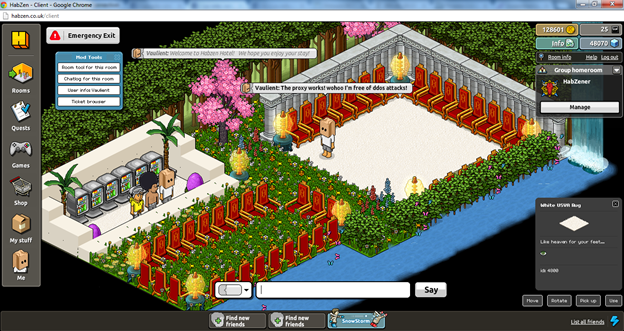
So now your DDOS proxy is set up perfectly and you're cheering with joy, what else should you do? Tell your friends!
You will want to purchase a proxy from the DDOS range, these can be found:
You must be registered for see links
. These servers are located in the US and are ideal for US based emulation servers.
When buying the DDS protection you will be guided to a popup which would option you to enable SSL and ipv6. They are not important for Habbo Retro, they may however be useful if you are going to run your site through the proxy as well. However these features are beyond the scope of this tutorial.
2nd step:

Once you completed the purchase process, you will be brought to the purchase complete page where it will ask you to edit your domain DNS settings. That is not necessary when it comes to a Habbo Retro, as the client does not connect using a domain name. Only people who are also hosting their site on the DDOS protection need to follow these instructions. So I would suggest you to ignore them to begin with.
3rd step:
Navigate to the dashboard, click on the services page in below dashboard in the header. Next to your service IP is an actions drop down. Click on edit in this dropdown.

After you have clicked on edit, you should be having a page like this

Your service currently contains all the default ports required for a proxying (protecting) a web page and mail service. However it does not have the ports required for a Habbo retro. To add these ports first delete the existing ports, this is optional but recommended since you won’t be using them. Then click the add port button and fill out the following settings.

Where 30000 is, is your hotel port. And where “YOUR-IP” is your hotel IP. When done click and and your settings should now look something like below.

4th Step:
Now that you have configured your TCP proxy click on save. Now go back to your CMS and head towards your client.php (for REVCMS) and for UberCMS it should be in class.config.php or ubercms_config.php for UberCMS 2.0.1. Now search for your connection info host.

This is my client.php it looks like this (above), it should look similar for others as well.
Put your proxy IP in your connection.info.host and the connection.info.port should be 30000 (or whatever you entered on X4B), in the end it should look something like this:

Save your client.php and you are done.
NOTES / DEBUGGING:
You might be wondering what IP should be the server IP in your config, well it should be your VPS IP. With your client IP proxied , nobody can get your real IP so there is no need to worry and what about the emu ? That should be your server IP as well. In your emu config , your game.tcp.port must be must match the port you entered on X4B.
Are you using phoenix emulator? Well there is no need to worry about it at all, since your TCP port has to be 1232 since Aaron forced it to be that way. Just replace all references to port 30000 in this tutorial with 1232.
For more information see:
You must be registered for see links
Conclusion:
Save your client.php and start your emulator , then click on enter client on your hotel and you should be logged on like me:


So now your DDOS proxy is set up perfectly and you're cheering with joy, what else should you do? Tell your friends!