Matiasvm
New Member
- Dec 23, 2016
- 3
- 3
Hi guys,
Today I share a cms that I created recently, the design I did thinking about the r63 (that's why the name "After"), with the vertical menu on the left, I hope you like.
The only problem is that it is in Spanish since I am from Colombia, I am sorry.
Sorry for my lousy english
Details.
Images

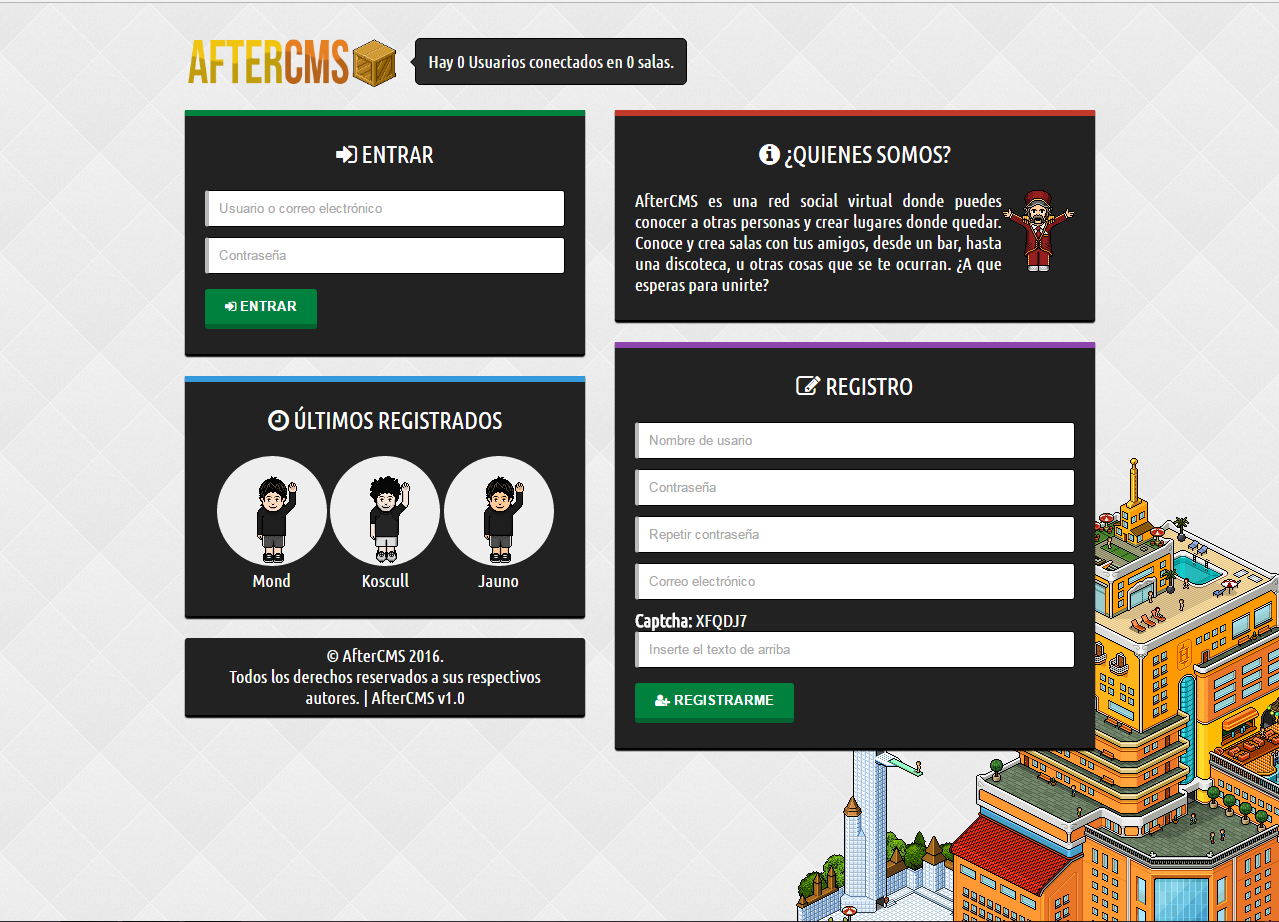
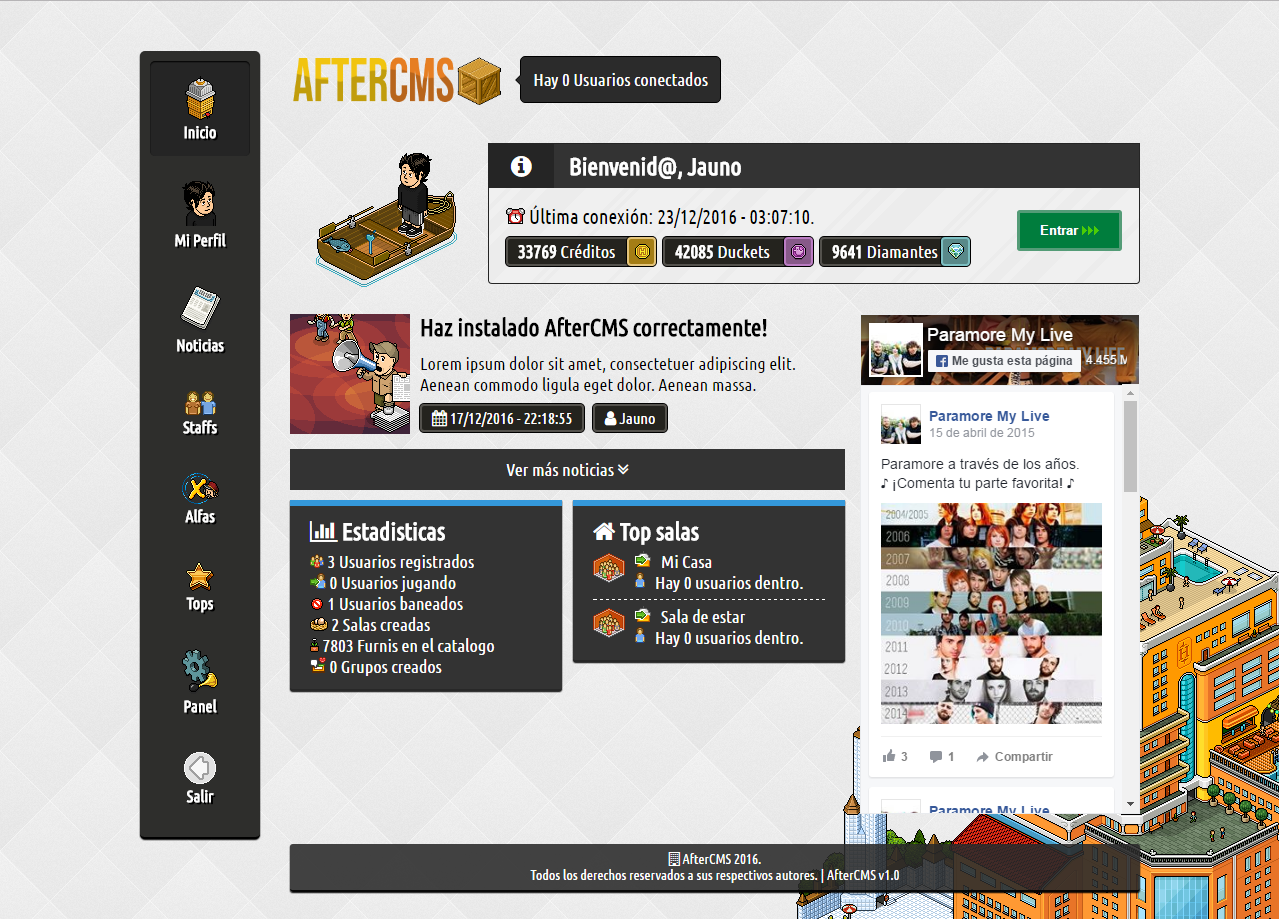
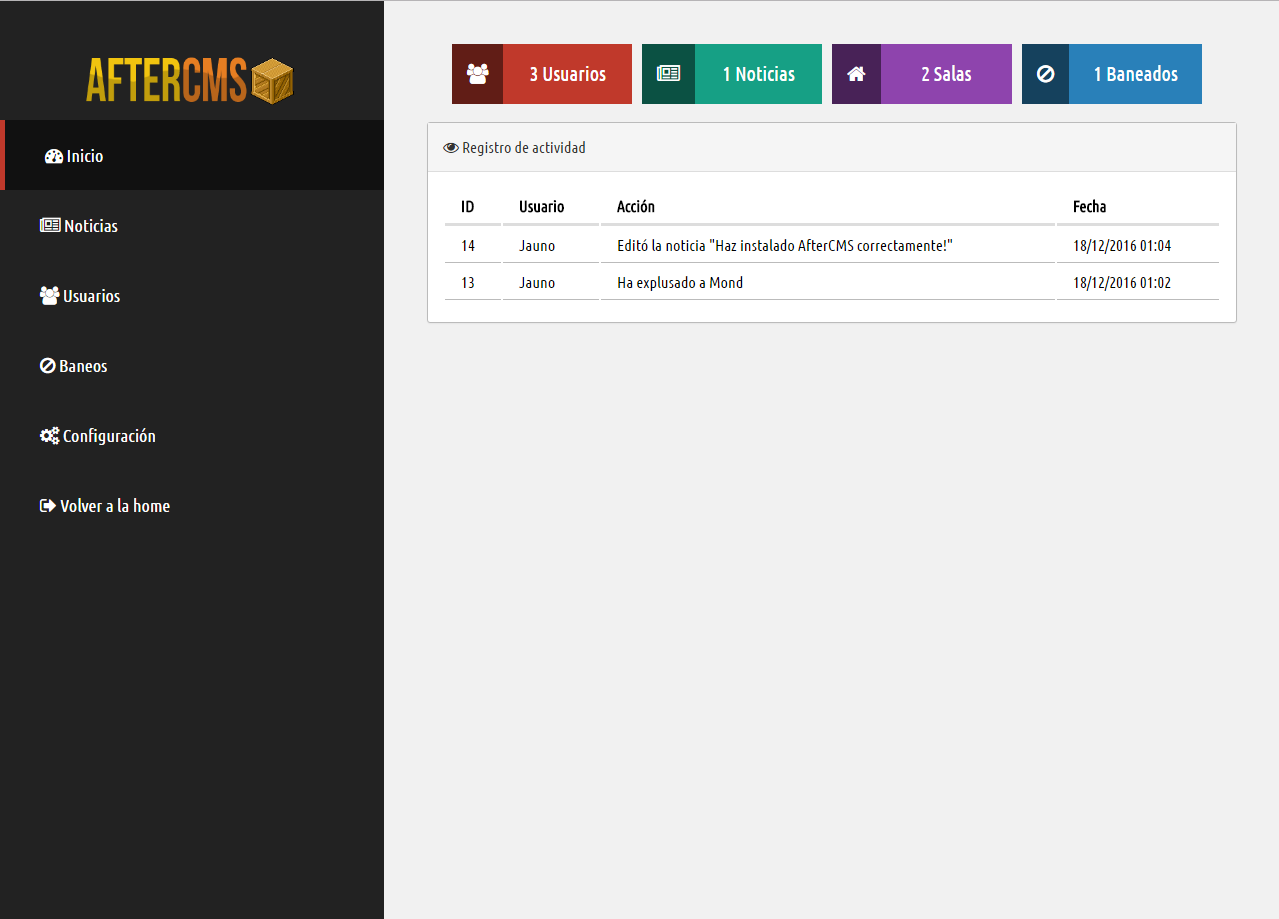
More images:
Download:
VirusTotal:
How to install:
- Upload the clean database of Plus Emulator and then the database of cms.
- Edit the file protected/config.php and client.php
Credits:
- Jauno (Matiasvm) (Programming and design)
- Habbo (Images)
Today I share a cms that I created recently, the design I did thinking about the r63 (that's why the name "After"), with the vertical menu on the left, I hope you like.
The only problem is that it is in Spanish since I am from Colombia, I am sorry.
Sorry for my lousy english
Details.
Code:
- Login and register on index.
- 2 Index designs.
- News.
- Comments for facebook plugin.
- Top users.
- Team page.
- Profile Settings
- Housekeeping 70%.Images




More images:
You must be registered for see links
Download:
You must be registered for see links
VirusTotal:
You must be registered for see links
How to install:
- Upload the clean database of Plus Emulator and then the database of cms.
- Edit the file protected/config.php and client.php
Credits:
- Jauno (Matiasvm) (Programming and design)
- Habbo (Images)



 ) van you share it?
) van you share it?